Application Settings Screen
Click on the Administration link in the left-hand menu to expose a link to the Application Settings screen. The applications settings screen provides access to a number of configuration options. The screen is broken up into a set of tabs representing functional areas. This screen shows the current settings within the system.
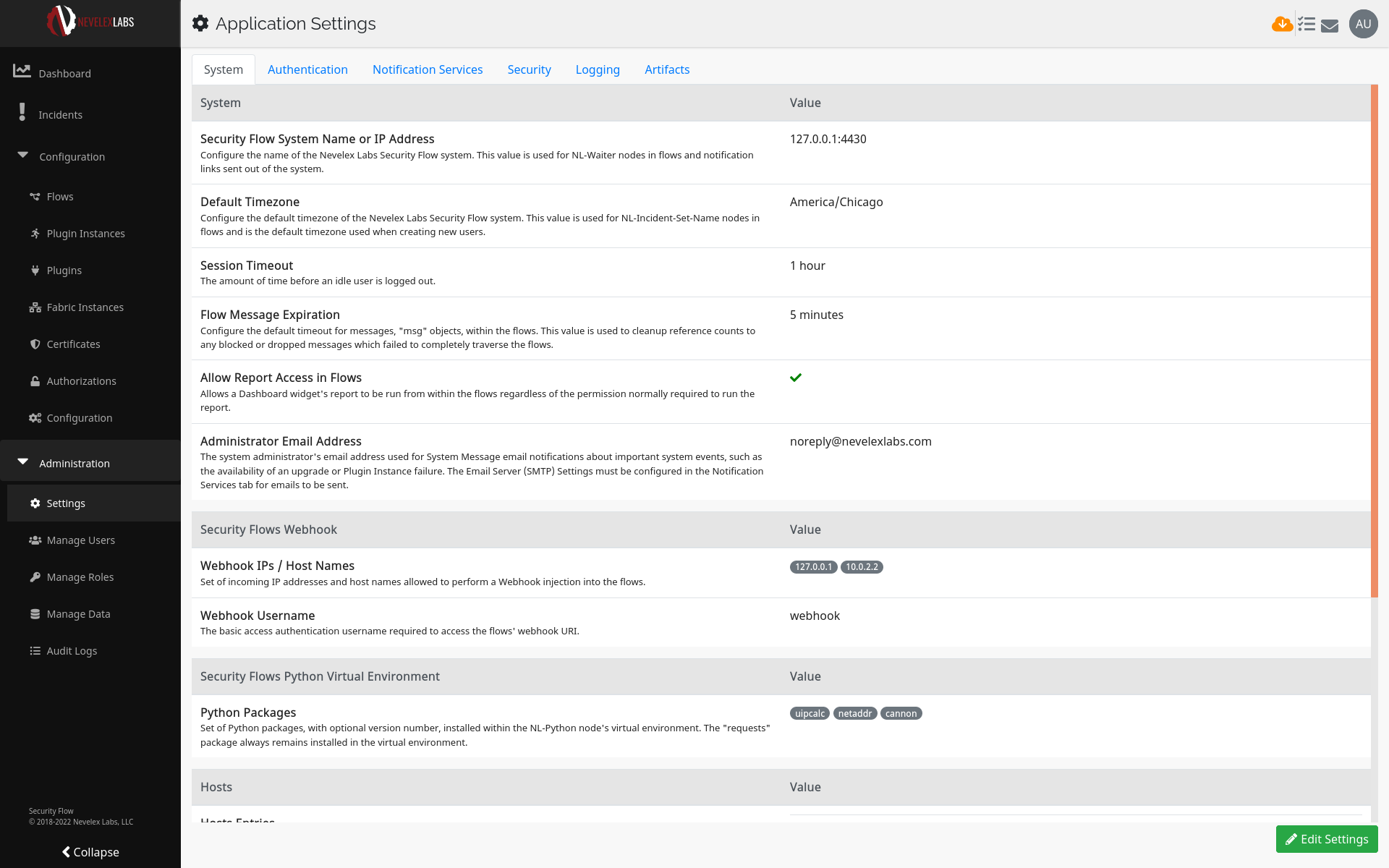
The following tabs and sections are available for configuration. Section options are detailed below.
| System Tab | |
|---|---|
| Section | Summary |
| System | Configures the Security Flow System Name or IP Address, Default Timezone, Session Timeout, Flow Message Expiration, Report Access in Flows, and Administrator Email address. |
| Security Flows Webhook | A webhook is used to inject messages into the Security Flow Flows engine using an HTTP operation from an external source, such as a script or external tool. Manage the list of IP addresses or host names allowed to be a source for HTTP requests into a flow and the username/password configuration for submitting an HTTP request. |
| Security Flows Python Virtual Environment | Manage the list of PyPI, the Python Package Index, packages which are installed. |
| Hosts | Manage the /etc/hosts file, a simple text file that associates IP addresses with host names. |
| System Update | Update the Nevelex Labs Security Flow software installation. |
| High Availability |
Allows for the management of high availability settings, such as Warm Standby Mode.
This section is restricted to super-users.
|
| Authentication Tab | |
|---|---|
| Section | Summary |
| Authentication Service | Configures Nevelex Labs Security Flow to use built-in, LDAP, or Single Sign-On for user authentication. |
| LDAP Server | The LDAP Server settings are shown when the Authentication Service is set to LDAP Server. |
| Single Sign-On (SSO) | The SSO settings are shown when the Authentication Service is set to Single Sign-On (SSO). |
| Notification Services Tab | |
|---|---|
| Section | Summary |
| Notification Settings |
Configures System Message notification preferences.
System Message notifications are displayed on the right side of Security Flow title area shown by clicking the icon. System messages are generated in one of two ways:
|
| Email Server (SMTP) Settings | Email Server (SMTP) Settings for sending a System Message notification via an outbound email. |
| Google Chat | Google Chat settings for sending System Message notifications to a space or chat. |
| Microsoft Teams | Microsoft Teams settings for sending System Message notifications to a channel. |
| Slack | Slack settings for sending System Message notifications to a channel or direct message. |
| Security Tab | |
|---|---|
| Section | Summary |
| Certificate Verification |
Enable or disable the verification of TLS/SSL certificates when connecting to services.
This section is restricted to super-users.
|
| Web Server Certificate | Manage the certificates used by Nevelex Labs Security Flow's website. |
| Logging Tab | |
|---|---|
| Section | Summary |
| SysLog Settings | Configures SysLog Settings for communicating with a remote SysLog server. |
| DXL Logging | Audits Incident related communication of various activities which occur on a DXL fabric. |
| Nevelex Labs Logging | Enables or disables verbose Auditing of Incident related communication which occurs on a DXL fabric to and from a Plugin. |
| Artifacts Tab | |
|---|---|
| Section | Summary |
| Indicators of Compromise | Configures the number of days until various Indicator of Compromise types reset to an Unknown (5) value. |
Section Details
The following sections describe the options available within each section in detail.System
| Options | Description |
|---|---|
| Security Flow System Name or IP Address | Configure the name of the Nevelex Labs Security Flow system. This value is used in NL-Waiter nodes in flows and notification links sent out of the system. |
| Default Timezone | Configure the default timezone of the Nevelex Labs Security Flow system. This value is used within various nodes in the flows and is the default timezone used when creating new users. |
| Session Timeout | The amount of time before an idle user is logged out. |
| Flow Message Expiration | Configure the default timeout for messages, msg objects, within the flows. This value is used to cleanup reference counts to any blocked or dropped messages which failed to completely traverse the flows. |
| Allow Report Access in Flows | Allows a Dashboard widget's report to be run from within the flows regardless of the permission normally required to run the report. |
| Administrator Email Address | The system administrator's email address used for System Message email notifications about important system events, such as the availability of an upgrade or Plugin Instance failure. The Email Server (SMTP) Settings must be configured in the Notification Services tab for emails to be sent. |
Security Flows Webhook
The Nevelex Labs Security Flow system is configured with a default webhook username and password for basic authorization. See the Webhook Injections Screen for more information.
| Options | Description |
|---|---|
| Webhook IPs / Host Names | Set of incoming IP addresses and host names allowed to perform a Webhook injection into the flows. |
| Webhook Username | The basic access authentication username required to access the flows' webhook URI. The URI is defined within the flow by using an http in node. |
Security Flows Python Virtual Environment
The NL-Python node allows for the execution of Python 3.6 scripts within a jailed virtual environment. To support running scripts requiring additional packages, this section allows for the installation and removal of packages from PyPI, the Python Package Index.
requests package always remains installed in the virtual environment because it is required by the SecurityFlow class.
| Options | Description |
|---|---|
| Python Packages | Set of Python packages, with optional version number, installed within the NL-Python node's virtual environment. |
Hosts
Displays the user defined mappings in the /etc/hosts file, a simple text file that associates IP addresses with host names.
System Update
Nevelex Labs Security Flow checks twice a day for the system updates. This setting sections allows for the downloading and installation of an update.
| Options | Description |
|---|---|
| System Update Step |
Shows the buttons for the three step upgrade process. The enabled button is based on the current state of the system update.
The three steps are:
|
High Availability
| Options | Description |
|---|---|
| Enter Warm Standby Mode | Warm Standby Mode deactivates most services within this Security Flow instance. A minimal UI is left operational to reactivate this instance. Entering Warm Standby mode disables all Security Flows. |
Authentication Service
By default, the LDAP Server and Single Sign-On (SSO) are disabled and users are managed within Nevelex Labs Security Flow. However, it is strongly recommended that LDAP or SSO be enabled to allow for user authentication to be managed by externally. When either LDAP or SSO is enabled, all user authentication is externally managed except for the default super-user, admin, and any existing user created whenBuilt-In Authentication was in use.
| Options | Description |
|---|---|
| User Authentication Service | The service used to authenticate users into Security Flow. LDAP or Single Sign-On (SSO) are the recommended options. |
LDAP Server
| Options | Description |
|---|---|
| LDAP Hostname | Set the LDAP Hostname URL to use for user lookups. |
| Port | Port to use when connecting to LDAP server. Defaults to port 389. |
| LDAP Search DN | Search DN to find the LDAP users or group. For example, cn=Users,dc=yourdomain,dc=com. |
| LDAP Filter Field | LDAP field which specifies the username. For Active Directory, this is normally sAMAccountName or userPrincipalName. For OpenLDAP, this is normally uid. |
| LDAP Group DN | Fully-qualified DN of the groupOfNames group. Must be under the LDAP Search DN tree. For example, cn=mygroup,cn=Users,dc=yourdomain,dc=com. |
| Encryption Method | Encryption method to use to connect to LDAP server. Supports LDAPS (LDAP over SSL) and StartTLS. |
| Authentication Method | Authentication method to use to connect to the LDAP server. Simple is the only supported method. |
| Authentication Bind DN/Username | Bind DN or username to use to authenticate to the LDAP server. |
| Authentication Password | Password to use to authenticate to the LDAP server. |
| Confirm Authentication Password | Shown in the Edit Settings screen to confirm the Authentication Password. |
Single Sign-On (SSO)
Used to configure SSO using SAML 2.0. The SSO Identity Provider will need the Single Sign-On URL, a.k.a. SAML Assertion Consumer Service (ACS), and Entity ID. Those values are in the following table.
| Metadata | URL | Description |
|---|---|---|
| Single Sign-On URL | https://[hostname]/v1/sso/acs/ | The Single Sign-On URL, a.k.a. SAML Assertion Consumer Service (ACS). Replace [hostname] with the hostname of the Security Flow instance. |
| Entity ID | https://[hostname]/v1/sso/metadata/ | Entity ID, a.k.a. Audience URI. Replace [hostname] with the hostname of the Security Flow instance. |
| Attribute Name | Type | Description |
|---|---|---|
| first_name | Basic | The user's first name. |
| last_name | Basic | The user's last name. |
| Basic | The user's email address. |
| Options | Description |
|---|---|
| SSO Strict | Configures the SSO module to strictly follow the SAML 2.0 standard. Additionally, rejects unsigned or unencrypted messages if configured to be signed or encrypted. |
| Name ID (username) Format | Specifies the format constraints on the username of the SSO user. Possible values are Unspecified or Email. |
| Service Provider Certificate | Shown in the Edit Settings screen. The Service Provider's (SP's) X.509 public certificate file in PEM format. The Service Provider is Security Flow. |
| Service Provider Private Key | Shown in the Edit Settings screen. The Service Provider's (SP's) X.509 private key file in PEM format associated with the public certificate. This private key must not be password protected. The Service Provider is Security Flow. |
| Identity Provider Entity ID | Fully specified URI of the Identity Provider's (IdP) entity ID. |
| Identity Provider SSO Endpoint | Fully specified URI of the Identity Provider's (IdP) SSO endpoint. |
| Identity Provider SSO Endpoint Binding | Protocol binding used by the Identity Provider's (IdP) SSO endpoint. |
| Identity Provider Public Certificate | Shown in the Edit Settings screen. The Identity Provider's X.509 public certificate file in PEM format. |
| Technical Contact Name | Metadata supplied to the Identity Provider. The name of the technical contact. |
| Technical Contact Email | Metadata supplied to the Identity Provider. The email address for the technical contact. |
| Support Contact Name | Metadata supplied to the Identity Provider. The name of the support contact. |
| Support Contact Email | Metadata supplied to the Identity Provider. The email address for the support contact. |
| Organization Name | Metadata supplied to the Identity Provider. The name of the organization. |
| Organization Display Name | Metadata supplied to the Identity Provider. The display name of the organization. |
| Organization URL | Metadata supplied to the Identity Provider. The URL for the organization. |
Notification Settings
| Options | Description |
|---|---|
| System Message Notification Severity | The minimum severity level for a System Message email notification being sent to the Administrator Email Address. This severity is the default used for any user account. The Email Server (SMTP) Settings must be configured for emails to be sent. |
| System Message Notification Resend | Defines the number of System Message occurrences which trigger a resend of an email. The resend logic is only applied if the minimum severity level is reached. This resend logic is the default used for any user account. The Email Server (SMTP) Settings must be configured for emails to be sent. |
Email Server (SMTP) Settings
| Options | Description |
|---|---|
| Email Server Host | The host name or IP address of the SMTP email server. |
| Email Server Port | The port of the SMTP email server. |
| Email Server Username | The username for authenticating with the SMTP email server. |
| Email Server Password | The password for authenticating with the SMTP email server. |
| Email Server Password Confirmation | Shown in the Edit Settings screen to confirm the Email Server Password. |
| Email Server Encryption Type | Type of encryption to use to communicate with the email server: SSL, TLS or None. |
| Test Service | Shown in the Edit Settings screen to send a test email to the currently set Administrator Email Address. Manually check the mailbox to ensure the message is received. |
Google Chat
| Options | Description |
|---|---|
| Service Configured | Indicator showing when a service is configured. |
| Webhook URL | The URL of the Google Chat Webhook. See https://developers.google.com/chat/how-tos/webhooks for details on setting up the webhook within Google Chat. |
| Test Service | Shown in the Edit Settings screen to send a test message to this notification service using the current webhook URL. Manually check the service to ensure the message is received. |
Microsoft Teams
| Options | Description |
|---|---|
| Service Configured | Indicator showing when a service is configured. |
| Connector Webhook URL | The URL of the Microsoft Team Webhook Connector. See https://docs.microsoft.com/en-us/microsoftteams/platform/webhooks-and-connectors/how-to/add-incoming-webhook for details on setting up the connector within Microsoft Teams. |
| Test Service | Shown in the Edit Settings screen to send a test message to this notification service using the current webhook URL. Manually check the service to ensure the message is received. |
Slack
| Options | Description |
|---|---|
| Service Configured | Indicator showing when a service is configured. |
| Connector Webhook URL | The URL of the Slack Webhook. See https://api.slack.com/messaging/webhooks for details on setting up a Slack app and webhook within Slack. Creating a new app followed by the creation of a webhook to the desired channel is all that is needed. The app should not be added to the Slack App Directory. |
| Test Service | Shown in the Edit Settings screen to send a test message to this notification service using the current webhook URL. Manually check the service to ensure the message is received. |
Certificate Verification
Verify SSL certificates when making requests to external services. Changing this setting will restart all plugin instances. WARNING: Disable at your own risk. Verifying certificates prevents man-in-the-middle attacks (MitM).
Web Server Certificate
The web server comes with a self-signed certificate for TLS access to Nevelex Labs Security Flow. For the system to function without requiring the user to bypass certificate authentication, certificates from a trusted CA should be installed. The other option is to manually trust the certificates and/or install the certificates as trusted within their browser across all users with access to Nevelex Labs Security Flow.
| Options | Description |
|---|---|
| SSL Certificate | Provides two button options. Use the Upload New Key Pair button to update a certificate from a trusted Certificate Authority (CA). Use the Generate New Self-Signed Certificate button to create a self-signed certificate. |
SysLog Settings
| Options | Description |
|---|---|
| Enable Remote SysLog | Set to enable logging to a SysLog host. |
| SysLog Host | The address of the SysLog server in host:port or host name format.
The SysLog host must accept TCP connections.
|
DXL Logging
On a DXL fabric, there are events generated by the fabric which may not need to be logged by the flows. These settings will, by default, disable logging of those events when they get fed into or sent out of the NL DXL Event In and NL DXL Event Out nodes. These settings are applied to DXL requests as well.
| Options | Description |
|---|---|
| Audit DXL Broker Client Registry Events | Activate to enable auditing of event messages for DXL Client registrations. This setting applies to DXL topics starting with /mcafee/event/dxl/clientregistry/. |
| Audit DXL Broker Health | Activate to enable auditing of event messages querying the DXL Broker Health. This setting applies to DXL topics starting with /mcafee/service/dxl/broker/health. |
| Audit DXL Broker Registry Events | Activate to enable auditing of event messages for DXL Broker registrations. This setting applies to DXL topics starting with /mcafee/event/dxl/brokerregistry/. |
| Audit DXL Broker Service Registry Events | Activate to enable auditing of event messages for DXL Service registrations. This setting applies to DXL topics starting with /mcafee/event/dxl/svcregistry/. |
Nevelex Labs Logging
| Options | Description |
|---|---|
| Audit DXL Plugin Instance Communication | Activate to enable verbose auditing of communication between Nevelex Labs nodes and Plugin Instances. When activated, messages sent to and received from Plugin Instances are included in Incident audit trails. |
| Audit Nevelex Labs DXL Messages | Activate to enable auditing of message transformations by nodes logging to external services such as McAfee's ESM SIEM. |
Indicators of Compromise
| Options | Description |
|---|---|
| Domain Trust Level Reset | The number of days before a domain IoC's Trust Level is reset back to Unknown (5). A value of zero (0) days will never reset the Trust Level back to Unknown (5). The NL-* IoC nodes may be configured to override this default. |
| IP Address Trust Level Reset | The number of days before an IP Address IoC's Trust Level is reset back to Unknown (5). A value of zero (0) days will never reset the Trust Level back to Unknown (5). The NL-* IoC nodes may be configured to override this default. |
| URL Trust Level Reset | The number of days before a URL IoC's Trust Level is reset back to Unknown (5). A value of zero (0) days will never reset the Trust Level back to Unknown (5). The NL-* IoC nodes may be configured to override this default. |
Application Settings Edit Screen
Click the Edit Settings button to edit the application settings.
Metro Office Park
2950 Metro Drive, Suite 104
Bloomington, MN 55425
Phone: +1 952-500-8921
©Nevelex Labs, LLC. 2018-2026, All Rights Reserved.
EULA